What are Ghost Calls and what can you do to prevent them.
 There
has been a noticed increase in the number of ghost calls. There are
several reasons that you might receive these types calls.
There
has been a noticed increase in the number of ghost calls. There are
several reasons that you might receive these types calls.
Ghost or Phantom Call- a phone call that when a person answers finds there is no one on the other end of the call. These calls contrast with silent calls where call centers place a call with no readily available agents.
The most likely is that a test call is made to your number for reasons of building a contact database. However, some scans take place to discover network weaknesses. These represent the ways to identify the type of ghost call.
Calls with a caller ID number, but no one there. Phantom call traffic.
Similarities that point to what is most likely taking place:
- Circumstances: Local number as caller ID. The caller never
leaves a voicemail.
The caller ID number is spoofed so that caller ID details make it very hard to trace back to the originating carrier and caller. Calling the number may result in "The number has been disconnected."Or "You have reached a non-working number." Many of the phone numbers displayed as caller ID are selected because they are local to the number called. This increases the likelihood of that the call will be answered and verified. And on the list your number remains. - Calls that do show up in your CDR records. Checking your Call Records does show a call with the caller's (possibly spoofed) number. In this case you can block that number; however, the most likely result will be that the next test will be from a completely different number. Many legitimate outbound call centers call and disconnect if a live person does not pick up the phone. These legitimate companies usually abide by FCC rules.
- Calls that do not show up in CDR records. These types of calls are specific and are frequently the result of SIP scanners probing a phone system. (Note: See below.)
A call is received from a local caller ID. When answered The Call is Connected to a Call Center:
- Circumstances: A local number shows in Caller ID that when
answered then goes to a call center.
These types of calls frequently use spoofed numbers as a caller ID so there is no way to easily locate the caller. However, when answered the call will then connect to a call center agent after a noticeable minor delay, who then attempts to sell you something. Some of these call centers offer legitimate products and some are scam operations. The company that generates the outbound calls may or may not be associated with any one particular call center. Some regularly generate millions of outbound calls for numerous call centers, many of which are in a foreign country. The FCC has made efforts to stop the most abusive companies and enacted new requirements for carriers to enact that should ultimately eliminate calls that circumvent FCC rules.
Phantom Rings or Ghost Calls that are most likely SIP Scans:
- Circumstances: Calls that do not show up in the Call Detail Records or call logs. Occasionally there are rings or calls that actually derive from SIP scanners. These SIP scans are probing networks, IP phones and VoIP ATAs for potential weaknesses. Many result as rings on phones that look as calls that originate from three or four-digit extensions, like 100, 1000 or 1000 numbers. Or on an in-house PBX CDR often as "Received call xxxxxxxxxx from unknown host." When these types of scans occur they are often at night and the phone may ring constantly. The display might even show "SIPVicious" which represents the name of the scanner. If answered, there is no one at the other end.
- What to do if you experience rings from a SIP scan. First, ghost calls rarely come from a service provider rather, they are usually the result of a scanner probing SIP ports, primarily 5060. Scans are made sending SIP invites to random IP addresses looking for a reply. For an in-house PBX you should always ensure "best security practices" which should include setting a default incoming call rule to block unknown calls. Many hosted VoIP and SIP trunk providers offer instructions, depending on the phone or endpoint, to configure settings that will prevent these occurrences. Settings regularly include disabling "Allow IP Call" and enabling "Accept SIP Trust Server Only." Some devices can be configured to restrict the source IP and to only allow specific IPs. The IPs that you then will accept calls from should comprise of the addresses given to you by your provider.
How to prevent SIPVicious ghost calls.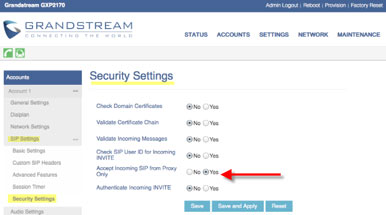
With
more work at home employees security risks increase. Hosted VoIP or
cloud PBX providers
routinely initiate very tight security control into their platforms that
result in very few intrusions. More limited companies that have their own PBX
phone systems typically lack specialized IT personnel. These smaller
companies often depend on in-house admin or a phone technician to ensure
systems and remote phones are secure. In all cases, ensure firmware of all devices,
like routers
and IP phones
have been updated. PBX
software should have all security patches installed regularly. International
Calling should be disabled if not needed and "best practices" enacted. Use
non-standard ports. The use of
VPNs for remote workers provides distinct advantages, as does the use of HTTPS
and SFTP.
Some IP phones include essential security settings to disable
direct IP calls. For instance, on a Grandstream GXP21xx phone, there is an
important security setting "Accept Incoming SIP from Proxy Only" that needs
to be set to Yes.
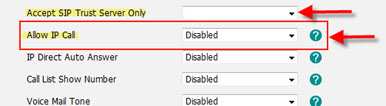 On Yealink
IP phones there are two settings;
"Accept SIP Trust
Server Only" needs to be set to Enabled and "Allow IP Call" to Disable. Both
settings should be found under the Features Tab on the General
Information Page.
On Yealink
IP phones there are two settings;
"Accept SIP Trust
Server Only" needs to be set to Enabled and "Allow IP Call" to Disable. Both
settings should be found under the Features Tab on the General
Information Page.
A "one-ring" phone scam that is different, but one you need to be aware of.
"One-ring" cell phone scam.
- A scam that has been on-going for several years and periodically resurfaces is distinctly different from other types of "phantom" calls. Scammers, many from west Africa, use auto-dialers to call primarily cell phones in the USA with only one ring. They then hope that the person that received the "missed call" will instantly call back. The number is an international toll number and will appear as a charge on your phone bill. The scammers then receive a large portion from the cost of the call. The FCC has issued alerts on this scam going back to 2014 and regularly issue updated warnings when the activity escalates.
Neighbor Spoofing
The term Neighbor Spoofing refers to calls made showing a caller ID with the first six digits, namely the area code and local exchange of your locality. The tactic is built upon the reasoning that you might be more likely to answer the call, believing it may be someone close by. These calls appear to look like they are coming from a local business or even a neighbor. Despite present laws preventing these strategies, government authorities caution that neighbor spoofing and robocall scams are currently on the rise.
Conclusion
 For those companies that have recently deployed work-at-home employees
connected to the office PBX, attention to security remains a high
priority. Keeping employees informed of security intrusions is
essential. Recently there has been an increase in all types of nefarious
activities, however, by remaining attentive to some of the techniques used,
companies can take precautions to reduce risks to a minimum.
For those companies that have recently deployed work-at-home employees
connected to the office PBX, attention to security remains a high
priority. Keeping employees informed of security intrusions is
essential. Recently there has been an increase in all types of nefarious
activities, however, by remaining attentive to some of the techniques used,
companies can take precautions to reduce risks to a minimum.
Best Practices to prevent unwanted access to your PBX.
Network best practices should include ensuring your phone system's security vulnerabilities are closed. Most breaches occur to easy targets. Those that are looking to gain access scan millions of IP addresses looking for the most vulnerable targets. Ten Tips for Better PBX Security.